We are committed to implementing appropriate security controls to protect data against unauthorized access, disclosure, or misuse. We ensure data security by encrypting data in transit and at rest, implementing strict access control measures, implementing regular backups, and enforcing strict password requirements. We also restrict access to data based on the need-to-know principle.
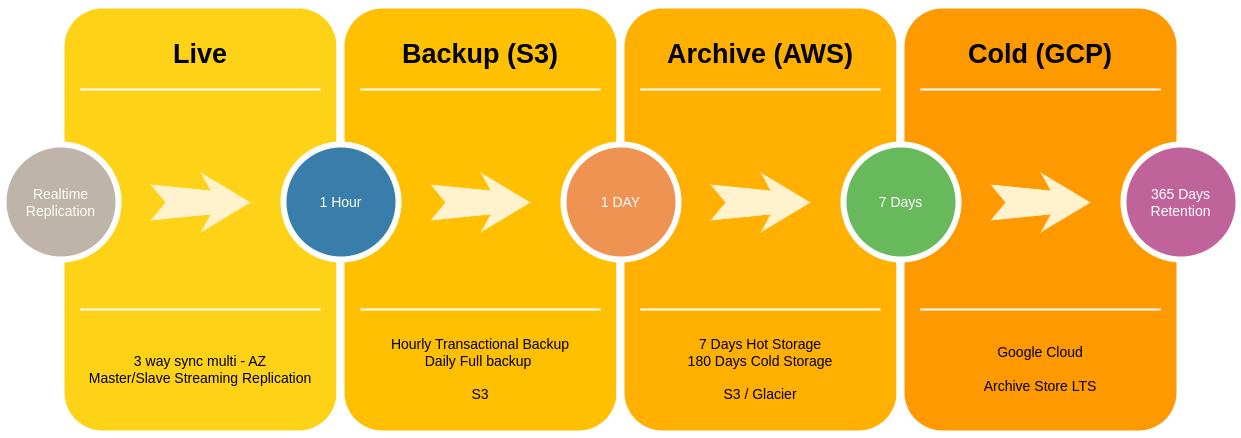
RPO – 1 Hour, RTO- 1 Hour
We execute nondisclosure agreements (NDAs) and assess third-party partners’ security controls regarding data protection before granting access.
High level overview of archive storage and recovery workflow.
Questions or comments about the Application may be directed to us by sending email to infosec@circlehd.com